Organizations are currently experiencing the most widespread unauthorized adoption of technology in corporate history. As Generative AI (GenAI) tools like ChatGPT, Copilot, and Gemini become increasingly integrated into day-to-day workflows, employees are often bypassing official policies and using these tools without formal approval or oversight.
This growing trend, known as Shadow AI, poses significant security and compliance risks. A survey by Telus Digital found that 68% of employees use personal GenAI accounts at work, and 57% have processed sensitive information through these tools. Even within the tech industry, the trend persists—Capgemini reports that 46% of developers are using GenAI, most without organizational authorization.
An analysis by Cyberhaven revealed that 73.8% of ChatGPT accounts used in the workplace are unsanctioned. As a result, IT departments are increasingly reporting issues related to data leaks, operational errors, and reputational harm stemming from unregulated AI usage.
Shadow AI is no longer an outlier—it’s becoming the norm. To effectively manage this evolving threat landscape, organizations must act quickly with clear governance policies, targeted risk mitigation strategies, and trusted technology partners. Datanet stands ready to support businesses in navigating these challenges and ensuring safe, compliant adoption of AI solutions.

What Are the Risks of Shadow AI?
Shadow AI is an extension of the term Shadow IT—the use of software or hardware without IT department approval—but with a specific focus on GenAI tools such as large language models (LLMs). Employees across all departments—from developers to marketing and support teams—are increasingly adopting AI applications to boost productivity. Beyond individual usage, many employees and even managers are purchasing these tools independently, bypassing the organization’s formal governance processes. The motivations vary: lack of approved alternatives, slow internal processes, or pressure to deliver results quickly.
However, the unauthorized use of GenAI introduces several critical risks:
- Data Leakage. Sensitive information may be stored in third-party logs (e.g., ChatGPT), exposing proprietary data such as trade secrets, business strategies, or access credentials. In public versions of ChatGPT, submitted private information can be used to generate responses for other users—potentially leading to unintentional data exposure and even copyright violations.
- Regulatory Noncompliance. Unauthorized GenAI usage can lead to violations of GDPR and other frameworks such as the NIS 2 Directive, exposing organizations to penalties of up to 4% of global annual turnover or €20 million—whichever is higher.
- Errors and Poor Decision-Making. Even a 2025 study by OpenAI indicates that advanced AI models like o3 and o4-mini still frequently produce “hallucinations”—false or fabricated information—which can lead to critical business errors if not properly vetted.
- Security Threats. Shadow AI tools often operate outside of organizational security controls and are not integrated with authentication, monitoring, or endpoint protection systems. Without formal onboarding, the risks of data breaches, unauthorized access, and lateral movement increase. AI tools can also be exploited as phishing vectors, for credential leaks, or internal data scraping. Open-source models introduce additional risks, such as prompt injection, adversarial manipulation, and unchecked plugins that expand an organization’s attack surface.
How Can Organizations Protect Themselves?
To mitigate the risks associated with Shadow AI, organizations must adopt a structured approach that combines clear policies, advanced technologies, and internal education.
Policy & Governance – Companies should implement well-defined AI usage policies that include:
- Data classification guidelines (e.g., public, internal, confidential, secret)
- Clear usage rules based on pre-approval (“ask permission” approach)
- Defined and approved AI use cases, differentiated by department and risk level (e.g., stricter controls for IT, Finance, Legal; more flexibility for Marketing or Support)
Monitoring & Active Detection – Deploying solutions such as CASBs (Cloud Access Security Brokers) and secure proxies with TLS inspection is essential for:
- Detecting and controlling access to cloud apps, including GenAI and Shadow IT
- Blocking or redirecting unauthorized traffic
- Gaining full visibility into app and data usage—including lawful temporary decryption of HTTPS traffic where justified
Access Control & Zero Trust Principles – Key control mechanisms should include:
- Multi-Factor Authentication (MFA)
- Internal network segmentation
- Port and protocol restrictions to protect critical assets and limit GenAI tool access only to verified users
Complementary Measures
- Ongoing employee training on AI risks and best practices
- Regular audits to identify unauthorized AI applications
- Encryption of data both in transit and at rest
- Clear BYOD (Bring Your Own Device) policies
- Implementation of SIEM and UEBA tools for detecting abnormal behavior linked to GenAI usage
This integrated approach empowers organizations to remain agile and innovative while maintaining strong security, data privacy, and regulatory compliance.
Control GenAI Usage with Cisco Secure Access

Cisco Secure Access, an integrated Security Service Edge (SSE) solution, offers a comprehensive set of capabilities that help organizations control and secure the use of Generative AI (GenAI) tools across the enterprise.
Key components include:
- Zero Trust Network Access (ZTNA): Provides secure, least-privilege access to applications—whether accessed from corporate-managed or personal devices—based on identity, device posture, and user context.
- Secure Web Gateway (Full Proxy): Inspects and logs all web traffic, delivering enhanced visibility, policy enforcement, and threat protection. Supports full or selective TLS decryption to inspect encrypted traffic safely.
- Cloud Access Security Broker (CASB): Detects, monitors, and controls the use of over 720 GenAI applications. Enables secure cloud adoption while restricting access to high-risk, non-compliant, or non-productive AI services.
- Data Loss Prevention (DLP): Continuously monitors sensitive outbound data to prevent leaks and unauthorized disclosures. It leverages over 1,200 pre-defined global identifiers covering 77 countries, ensuring compliance with regulations such as GDPR, HIPAA, PHI, PCI, and more.
- Firewall as a Service (FWaaS) with Intrusion Prevention System (IPS): Offers deep visibility and robust threat prevention across all user-to-application traffic—whether internet-bound or within private infrastructure—covering all ports and protocols.
In addition to these core capabilities, Cisco Secure Access features a dedicated AI Access function—designed specifically to govern employee use of GenAI tools and safeguard sensitive data. Leveraging the full power of Cisco Secure Access, AI Access delivers:
- Shadow AI Discovery – Monitors web traffic to detect unauthorized use of GenAI tools. Delivers a clear inventory of AI applications actively in use within the organization.
- Shadow AI Risk Assessment – Provides contextual risk analysis to support informed decision-making. Includes data on app usage, user devices, geolocation, and network attributes. A centralized dashboard highlights the riskiest applications with risk scores and actionable recommendations.
- Access Control & Data Protection – Enables granular access policies, blocks prompts that raise privacy or security concerns, and intercepts malicious responses that could propagate threats. Ensures secure and compliant use of third-party GenAI tools.
With Cisco Secure Access, organizations gain the visibility, intelligence, and control needed to embrace GenAI safely—empowering innovation while protecting data, users, and regulatory compliance.
Fortinet’s AI-Powered Defense: FortiAI-Protect
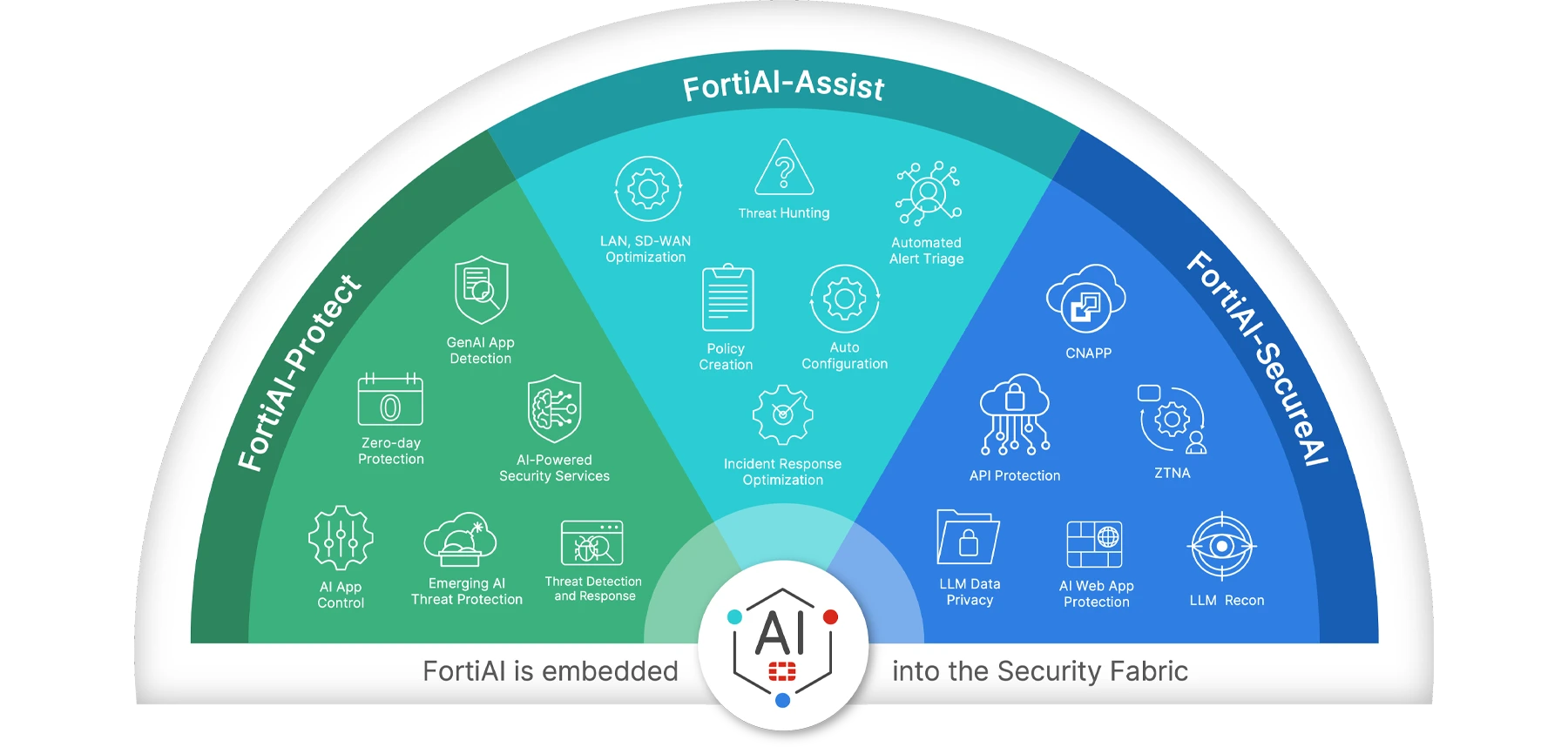
Fortinet’s FortiAI-Protect, recently presented by the Datanet Systems team, is a next-generation security solution designed to defend against AI-driven and emerging cyber threats. By leveraging advanced contextual risk analysis and automation, FortiAI-Protect reduces alert fatigue, blocks advanced attacks, and ensures secure, policy-driven use of GenAI applications—including those accessed outside official channels.
Key capabilities include:
- Full Visibility into GenAI and Shadow AI Use: Monitors traffic across more than 6,500 AI-related URLs, enabling real-time discovery and analysis of both sanctioned and unsanctioned GenAI applications.
- Access & Content Control with Zero Trust Principles: Empowers security teams to restrict high-risk or unauthorized AI tools through dynamic access controls and monitoring of AI-generated content.
- Granular Policy Enforcement: Applies security policies per application, automatically and at scale, using a robust catalog of over 6,000 pre-classified AI tools.
- ML-Driven Threat Prevention: Uses machine learning and large-scale behavioral analytics to detect and neutralize emerging malware and sophisticated attack techniques.
- Adaptive Intrusion Prevention: Continuously trains IPS models to recognize new attack vectors and defend against advanced persistent threats (APTs).
- Contextual Threat Intelligence: Correlates threat indicators across data streams to enhance incident response and reduce false positives.
Datanet Systems: Trusted Expertise in Shadow AI Governance
Shadow AI is quickly emerging as a critical attack vector—one that, if overlooked, can expose organizations to data breaches, regulatory violations, and reputational harm. Advanced solutions such as Cisco Secure Access and Fortinet FortiAI-Protect provide powerful capabilities to identify, manage, and mitigate the risks associated with unsanctioned GenAI tools.
As a Cisco Gold Integrator and certified Fortinet partner, Datanet Systems offers deep expertise in securing AI ecosystems. We support clients through strategic consulting focused on developing risk-informed GenAI policies, alongside the design and seamless integration of technologies like Cisco Secure Access and the Fortinet Security Fabric. Our teams also manage implementation, employee enablement, and the rollout of agile governance processes tailored to the specific needs and risk profiles of each organization.
By combining next-generation technologies with a structured, security-first approach, Datanet helps organizations adopt AI with confidence—ensuring innovation doesn’t come at the cost of compliance or control. Shadow AI isn’t a passing concern—it’s a pressing security imperative and Datanet Systems is your trusted partner in building a secure, compliant, and AI-resilient enterprise. For more information, please contact us at sales@datanets.ro.
 Datanet Systems participates as Gold...
Datanet Systems participates as Gold...
