 Cyber-attacks are becoming more sophisticated and force a similar trend to specialization those responsible for information security. No applications cannot lag behind, and companies need advanced solutions, capable of providing the entire infrastructure protection, and a high level of automation. Datanet Systems comes with a team of certified and experienced specialists, and a new generation solutions portfolio.
Cyber-attacks are becoming more sophisticated and force a similar trend to specialization those responsible for information security. No applications cannot lag behind, and companies need advanced solutions, capable of providing the entire infrastructure protection, and a high level of automation. Datanet Systems comes with a team of certified and experienced specialists, and a new generation solutions portfolio.
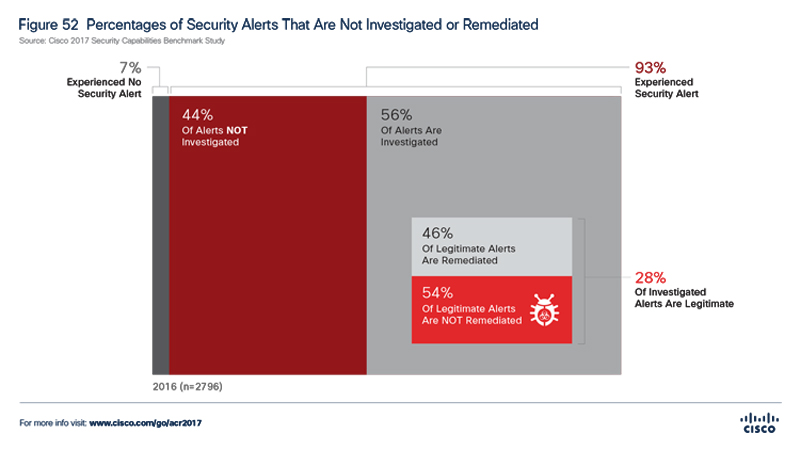
The organization’s perimeter security is constantly expanding because of the pressure that comes from the increased number of mobile employees and cloud services adoption. The expansion means also the increased exposure of the companies against advanced threats that are rapidly diversifying and are becoming more complex. In order to reduce information attacks and to keep the risk under control, more and more organizations allocate substantial investments and spend large amounts of energy. Marketing studies developed over the last few years confirm the continued increase for the budgets dedicated to information security, but results are not always according to the efforts made in this direction nor are the expectations. According to Security Capabilities Benchmark Study, part of the tenth edition of the annual Cisco Security (Cybersecurity Annual Report 2017), only 56% of companies are investigating security breaches faced in real-time. Of these, only 28% are legitimate and represent real threats. But what is worse, is that less than half (44%) of these identified problems are being addressed.
Critical challenges
The data highlights in the quoted survey shows the number of critical issues with a high incidence increased among organizations:
- On-time low capacity detection of vulnerabilities and threats;
- Spending a large volume alerts effort of “false positive”;
- Inefficiency in remediating threats identified/confirmed.
The causes of these problems are numerous and are often based on an inadequate approach to the security issues within organizations. A concrete example of this is the fact that 65% of security officers who participated in the Cisco study indicated that they use between 6 and 50 security products from various vendors.
Of course, diversity is needed – especially when trying to ensure independence from a particular vendor – and it is perfectly legitimate for any company to want to be protected by the highest rated product. But a mix of solutions – whether and “best of breed” – is not an automatic guarantee of protection against threats. In many cases, security infrastructure heterogeneity generates significant challenges due to the fact that most solutions are not interoperable and require special competence on the configuration, have a low level of backward compatibility that requires dedicated management tools, etc. All these minuses are cumulatively translated into a limited vision on the exposure level infrastructure and applications running on it, the behavior of end-users, potential gaps that could be exploited if a security incident occurs, the degree of compromise of a certain type of equipment and/or device sites, etc.
Experience is important
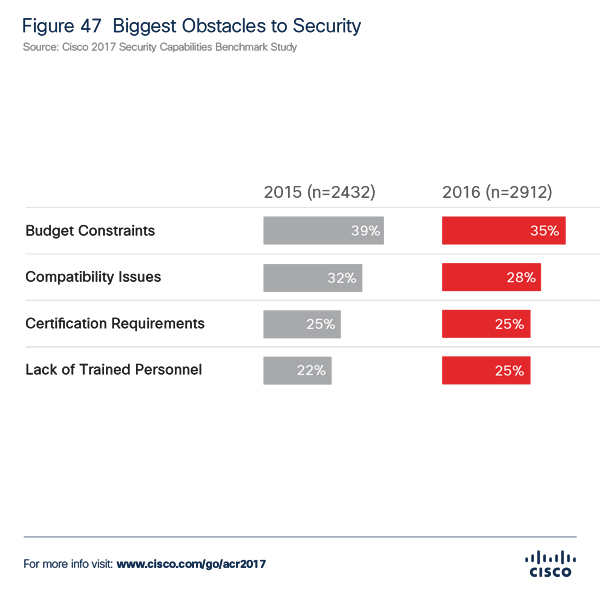
There are real problems, both in practice and confirmed by the fact that the top IT security challenges developed by specialists from Cisco on the compatibility of products (claimed 28%) rank second (after the budget). In the hierarchy of the problems that are faced, the next in line, in the same place is employees’ level certification and lack of trained personnel (each with 25%).
The specialists’ certification level is the second major problem that many organization is facing, compounded by a qualified workforce deficit in the field of information security. It is a global challenge, as evidenced in the latest study ISACA (State of Cyber Security 2017: Current Trends in Workforce Development), showing that for most companies (55%) experience is the most important criterion for employment of a specialist in security. The best solution in this scenario is identifying a partner with real expertise achieved after completing relevant projects. Thus, Datanet Systems comes with the relevant experience and competences and can provide the proper security level for each company.
Automation advantages in information security
Datanet Systems’ second competitive advantage is having a complete portfolio of new-generation information security solutions together with being the leading Cisco partner in Romania.
Because, beyond experience and certifications, advanced security solutions come with the advantage of extended visibility to the entire infrastructure, but also provide a high level of automation. This represents an important gain, especially for companies faced with both budget and specialized professional resources limitations. Automation is the best possible answer in the identification, analysis, and fast remediation of real threats, by increasing the efficiency of resource usability. Cisco information security solutions integrate automated services that enable customers to effectively manage not each individual alert or incident. For example, by using the Cisco Identity Services Engine (ISE) you can automatically authenticate and authorize each user and/or device that connects to a company’s network. ISE allows access to certain types of content and applications depending on the rights assigned to each user, type of equipment used, etc. Complementary, Cisco Advanced Malware Protection (AMP) provides continuous monitoring of network equipment and of end-users’ devices. Once identified as a potentially malicious file (either the signature or technology sandbox), Cisco AMP provides alerts and automatically performs a dynamic retrospective analysis to identify the source/breach created, the affected areas, and potential targets. Similarly, Cisco Lancope StealthWatch monitors and analyzes traffic patterns and automatically detects anomalies, identifying their source and by communicating with Cisco ISE places in quarantine the affected endpoints.
All these related automation improve the detection rate of threats and vulnerabilities (according to the latest statistics, Cisco recorded a higher score with an average time of detection of fewer than 6 hours), stops cyber-attacks, and limits the extension of the compromised area. But Cisco solutions have also a strong proactive component. For example, the continuous scanning services of the network components obtain an automatically-updated list of vulnerabilities in real-time, at the host and application level, and can prioritize interventions depending on the severity of the threats. This provides both an overall improvement in security levels, and increase operational efficiency in the IT department.
Information security personalized solutions
According to the security applications portfolio and the experience achieved in many information security projects, Datanet specialists can design and develop personalized architecture solutions according to each client’s needs.
For example, for a company that wants to adopt the “Work from home” model, so the employer can give his employees access to company’s resources, it can be developed a solution that covers data encryption and, with the help of Cisco Anyconnect Secure Mobility Client, it can be established if a user is or not within the company’s physical office. If he’s outside the company, the connection is automatically made through VPN, through ISE Posture Agent, while checking the security rules agreed previously. In case of noncompliance identification (antivirus system off and/or out of date, missing security patches, blocked DLP processes, etc.), the device is automatically placed in a quarantine area to fix the identified problem.
Why Datanet?
Datanet Systems has the experience and competences in delivering both Cisco and other security solutions. Datanet’s certified specialists in information security systems ensure the design, development, supply, commissioning and configuration solutions, providing complete consulting, maintenance, and specialized training.
For more information, please visit our dedicated section.
Contact:
Gabriel Mușat
Deputy Executive Director
office@datanets.ro
www.datanets.ro
 Why are the Companies adopting the new...
Why are the Companies adopting the new...
